Tl;dr - unfixed information disclosure in Prisma Cloud defenders
This post is about how to abuse a agent of a cloud security solution to get information which you should not know, like what security controls are applied, what assets the victim owns and the owners of the assets.
Introduction
A few months ago I was examining the Prisma Cloud configuration of my workplace and accidentally discovered an information disclosure issue of Prisma Cloud defender (the agent). This issue has been reported to Palo Alto as security disclosure, however Palo Alto declared that this is an expected behavior.
While Palo Alto seems not considering it as a problem, I think it is at least a trick for post exploitation. Below is some background knowledge.
Prisma Cloud
Prisma Cloud is a cloud security solution developed by Palo Alto, providing features including monitoring processes in standalone hosts/ run as daemon set in a K8S cluster.
This is done by deploying an agent (which is called a defender) in the target host.
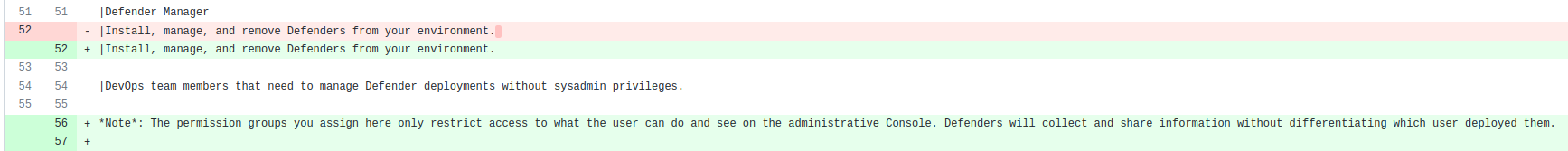
To do so, one needs permissions to Prisma Cloud in order to get an access token. Defender Manager is the most suitable role for an operator whose manager only wants him to help deploying defenders without letting him/ her know other information, for example monitoring rules.
Digging the hole host
Let’s get a Defender Manager role and install a host defender on a linux machine, let’s say machine A.
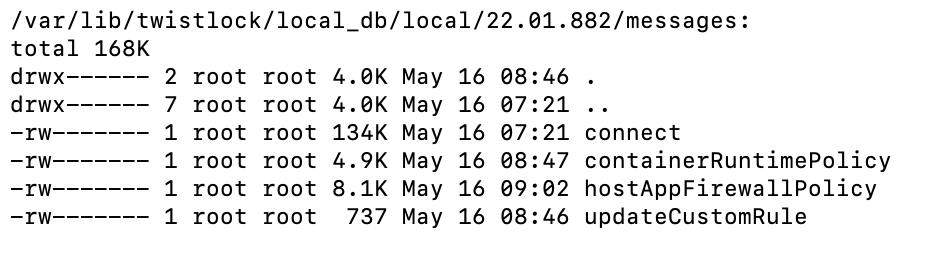
Take a look at the directory /var/lib/twistlock/local_db/local/<version number>/messages/, connect is a big file containing a lot of configs, while some details are stored in other files in the same directory.
Why can I view things that has nothing to do with my host?
- Other assets like container registries
/var/lib/twistlock/local_db/local/<version number>/connect

- Firewall rules that belongs to OTHER hosts
/var/lib/twistlock/local_db/local/<version number>/hostAppFirewallPolicy
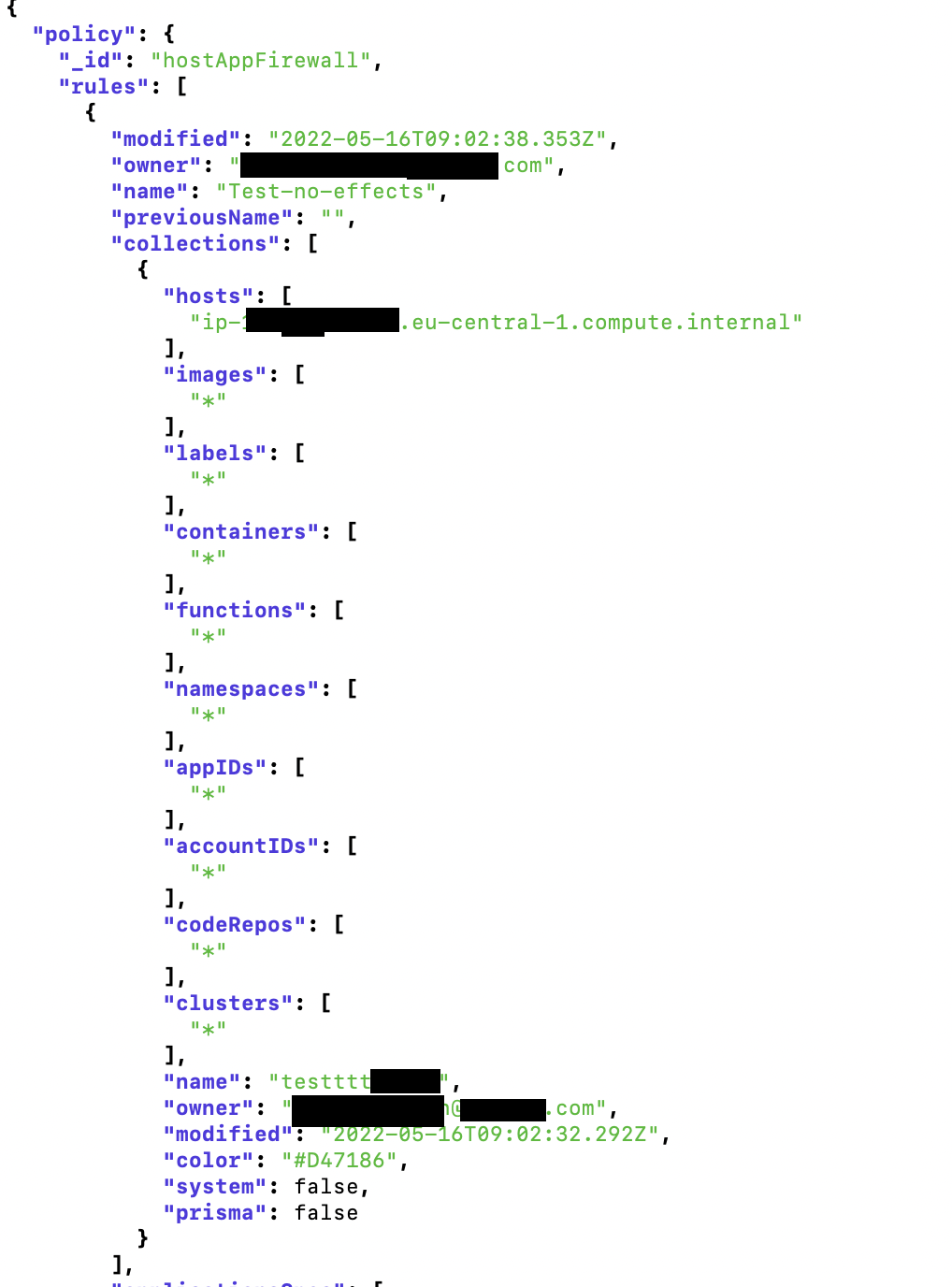
- Content of custom rules (e.g. process/ network monitoring)
/var/lib/twistlock/local_db/local/<version number>/updateCustomRule
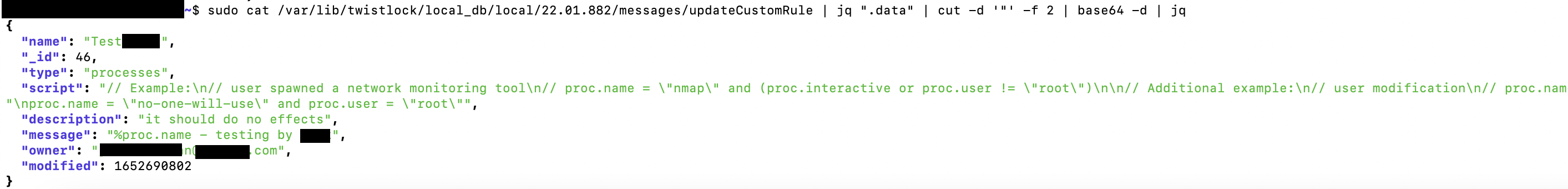
As a Defender Manager, all you are supposed to have is the root access in the host where the defender to be installed on. However, after installing defenders, you will be able to get information much more than just the info of that host. For example, reading custom rules on other hosts, let say, hosts which are more important and you don’t want to get caught when you have the chance to access them.
Those could help you if you are an internal threat of a company which uses Prisma Cloud but don’t know this trick :)